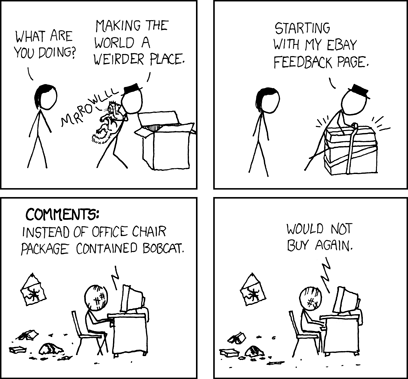
In the spirit of Shockwave Rider’s information-sharing worm, the charm of StumbleUpon, and this xkcd cartoon:
And based on the fact that QR codes are “teh awesome”, I have created something both wonderful, inspiring, and evil all at the same time: a Random QR Code Redirector. Just point your phone’s QR reader app at this barcode, sitback, and enjoy the mayhem. Sometimes you get a neat hack url, sometimes you get a funny movie, sometimes you get information about barcodes, sometimes you get something that “once seen, cannot be unseen”. Feel free to print them out and leave them places. =)
And ta-da, the barcode:

Readme, Clickme!!!
Get a QR reader and other QR Code infos here.
“How’s it all work?” Well, for starters I got a vanity domain at co.de (works swimmingly for software projects because, well, it’s “code”). Then I built a database and ~15 lines of php code. I make a weighted random select from the database and send a redirect to the browser.
Table create statement:
CREATE TABLE IF NOT EXISTS `qr_redirect_links` (
`id` smallint(3) NOT NULL auto_increment,
`url` varchar(1500) collate utf8_unicode_ci NOT NULL,
`weight` smallint(3) unsigned NOT NULL,
`comment` varchar(1500) collate utf8_unicode_ci NOT NULL,
PRIMARY KEY (`id`)
) ENGINE=MyISAM DEFAULT CHARSET=utf8 COLLATE=utf8_unicode_ci AUTO_INCREMENT=37 ;
The query code is as follows:
<?php
$con = mysql_connect(“<hostname>”,”<username>”,”<password>”);
if (!$con)
{
die(‘Could not connect: ‘ . mysql_error());
}
mysql_select_db(“random_urls”, $con);
//You could do a bunch of random select stuff in php but using the database Rand()*(1/Weight) is the easiest 1-liner I know to get a random result.
$result = mysql_query(“SELECT url FROM qr_redirect_links ORDER BY Rand()*(1/Weight) LIMIT 1;”);
while($row = mysql_fetch_array($result))
{
$newurl = $row[‘url’];
header( “Location: $newurl” ) ;//actually send the redirect here
}
mysql_close($con);
?>
I’m also collecting interesting urls, just email/twitter/whatever to me, the only rules are that they need to not harm the browser and I have final say on what meets my stringent url quality standards.
Similar Posts:
 1 Comment »
1 Comment » Posts RSS
Posts RSS




